
Most systems and web sites that I access on a regular basis support multi-factor authentication, which involves presenting multiple pieces of evidence as part of an authentication attempt, such as:
- Something you know (eg: a password)
- Something you have (eg: an authentication token)
Even though some sites that I access support push notifications with an easy approval process (such as Azure AD with Microsoft Authenticator and Duo), I still access quite a number of systems that require entering a one-time PIN (OTP) that is either generated by an authentication app or sent via SMS to my phone. Some days it feels like I spend more time entering OTPs than actually doing work.
For a while I have noticed that a growing number of sites are supporting hardware based tokens based on the FIDO2 Project (such as YubiKey) and for this reason I decided to look at purchasing a YubiKey and using this to access sites where possible.
There are a number of available models but I settled on the YubiKey 5 NFC as it supports both traditional USB authentication when connected to my computer, but can also be read by my Smartphone using NFC.
Ordering
Once I decided which model to purchase, I placed an order with Trust Panda and waited for the YubiKey to arrive.
I didn’t need to wait long. Trust Panda ship their stock from Sydney, so it arrived very quickly and was well packaged.

Getting Started
Once the key arrived I took a look at the Works with YubiKey Catalog to see where I could use YubiKey and started adding the key to each account.
The process is easy. Let’s take a look at GitHub:
Step 1
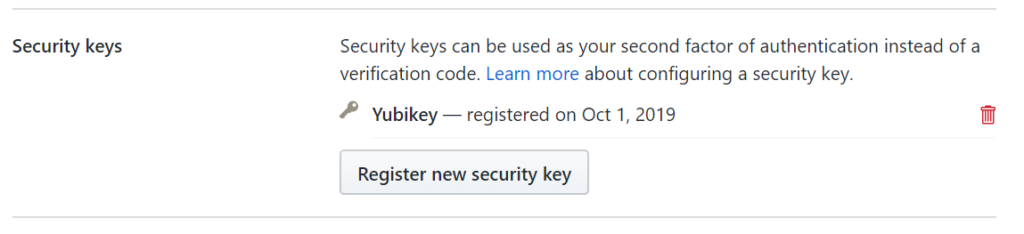
The first step requires accessing your Github security settings for two-factor authentication. Looking at my account, you can see that I am already using an authenticator app but I don’t have any security keys configured so I click “Add”.
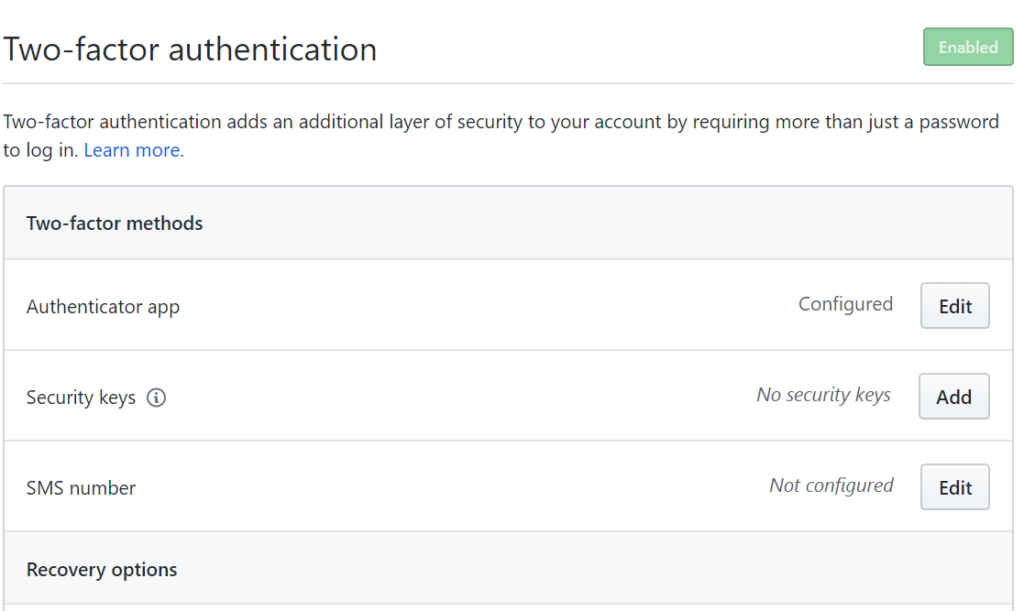
A popup will appear where you can click to register a new security key.
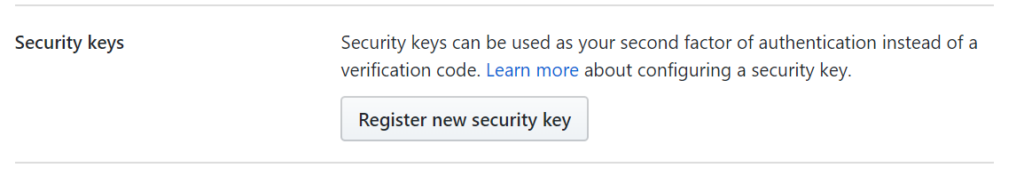
Step 2
To access the FIDO2 application on the key, you’ll need to enter a PIN. If this is the first time using the key you will be prompted to set an initial PIN.
This provides an extra level of protection as if the PIN is entered incorrectly 8 times in a row the authentication capability will be locked out and the key will become useless unless reset and you re-enrol the key with each site.
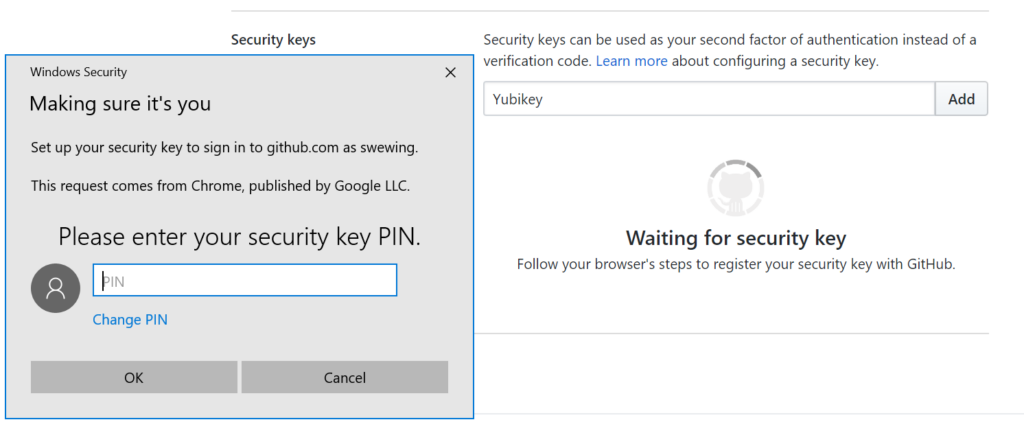
Step 3
With the correct PIN entered you are asked to touch the key. The YubiKey 5 NFC has a capacitive button that you touch to initiate the authentication flow.
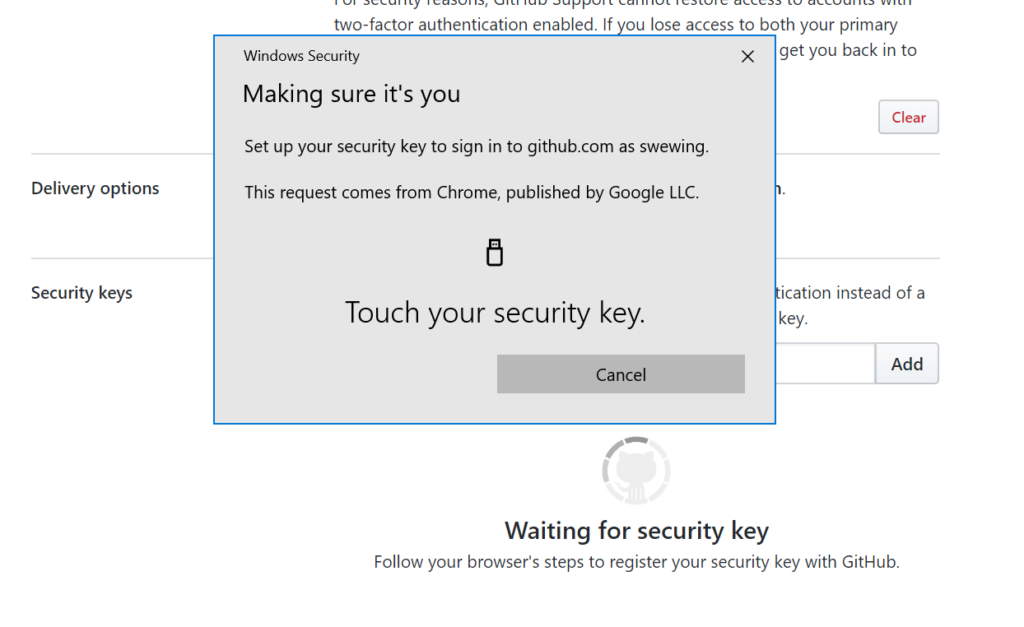
Step 4
If you completed the previous steps correctly you will have successfully enrolled the keys with GitHub (or another site that supports these keys)
Login Process
Once you have enrolled the key, logging in is quite easy.
If your account has a key associated, when logging in you will generally be asked to insert the security key if it’s not already inserted.
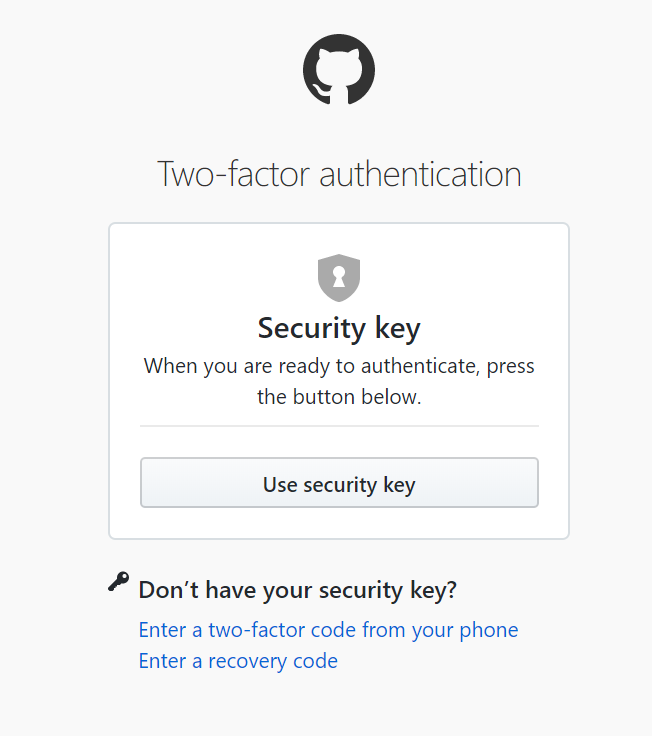
When you have selected the option to use the security key, you will receive a prompt to touch the button.
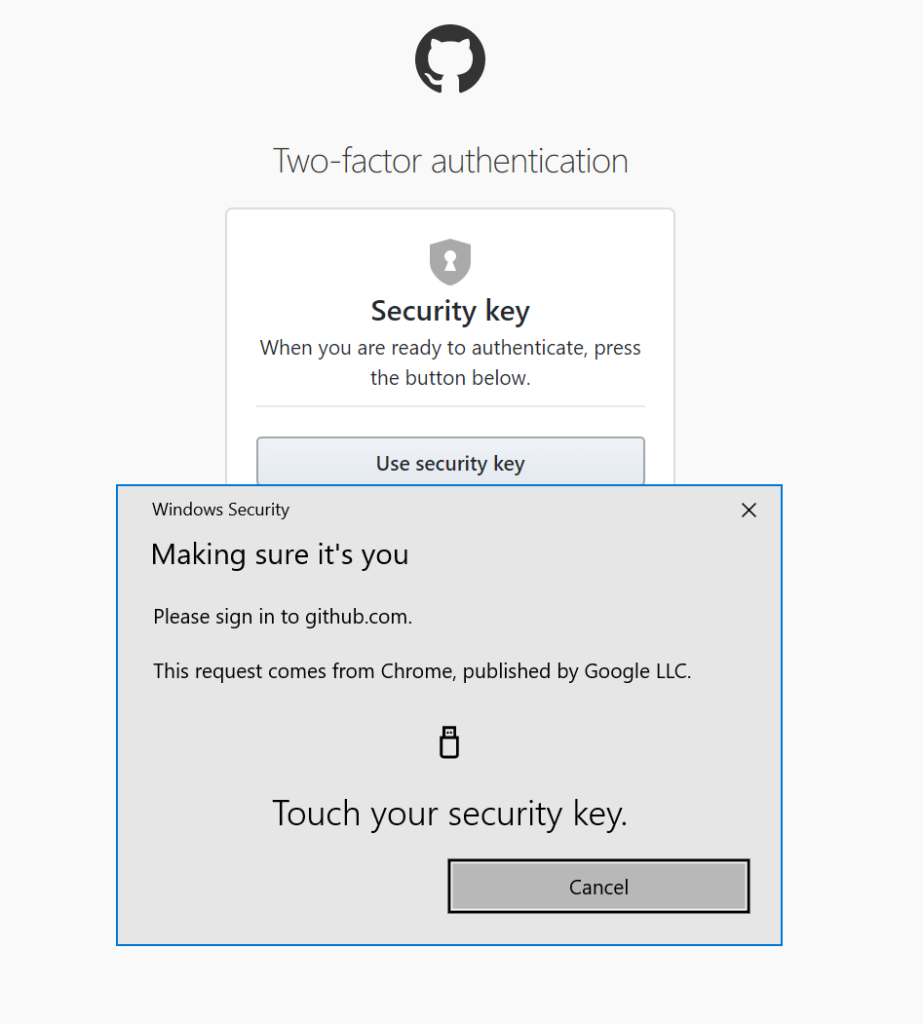
Once done and assuming the authentication has worked successfully you will then be logged in. It is so much easier and quicker than waiting for an SMS notification that may or may not arrive or opening an authenticator app, finding your token, and entering it into the site.
Conclusion
While it’s only early days, YubiKey is already saving me time when logging into various sites. As SMS can also be quite insecure due to the flaws in the mobile porting process I also feel safer using YubiKey authentication (with a backup OTP in my code generator) where possible. I don’t regret the purchase at all.